
Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.
86-0769-39020536
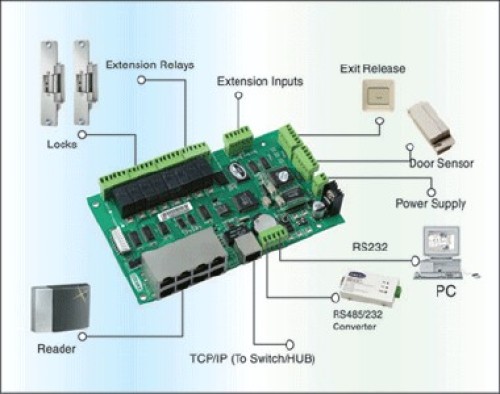
After more than 20 years of development, the access control system has surpassed the simple doorway and key management of the past and developed into a complete access management system. Through the computer system, when and where to release certain people, when and where to reject certain people, when to send out alarm signals and save access records, the access control system can achieve the purpose of security prevention and timely alarm linkage, and it is safe in the working environment. To play an important role in improving corporate management efficiency.
The development of the access control system combined with the development of access control technology and the security of the access control system, the access control industry has experienced several important development stages, mainly including low-frequency card technology and high-frequency card technology and the latest virtual credential card technology.
Low-Frequency Card Technology Access Control Systems For the past 15 or 20 years, low-frequency cards have become the standard in the security industry, providing efficient and effective access control. This kind of card structure is simple, who can use these cards to enter the building. Anyone who holds a company-issued card can enter the building; this person can be an employee who owns a company-issued card or uses a stolen or lost card to pass through the access control. In order to increase the security of low-frequency cards, companies add visual security information such as photos to their cards, employees wear ID/access cards with their own photos, and security personnel are also trained to verify personnel who do not have corresponding authentication information. To provide basic authentication methods. These low-frequency cards are often called proximity cards or ID cards and are easily copied today. Because illegal workers can copy low-frequency cards through certain devices, so they can enter and exit the building freely. Unless there is a surveillance camera in the building or someone has witnessed this person entering the building, it is impossible to know that unauthorized persons used to pass the access control and give access control systems. Security brings instability.
For security managers, resellers, integrators, and equipment manufacturers (OEMs), HID's 125 kHz RFID Prox card and reader are the industry standard for access control systems at this stage. HID proximity cards are reliable and affordable, and can be seamlessly integrated with access control systems.
Even today, HID Prox technology still offers a very good value for money and convenience. However, the 125 kHz RFID card technology and card format are not as secure as contactless smart cards, which has led to the development of access control systems to contactless smart card technology.
Contactless high-frequency smart card technology Access control system At present, the network access control system of non-contact high-frequency smart card technology is widely used in all walks of life, such as government departments, financial institutions, transportation, energy, intelligent communities, factories, hospitals and other fields. . By embedding multi-layer security elements in the smart card chip, managing all doors through the computer, setting up powerful access control management functions and permissions, real-time monitoring of the door's entry and exit conditions, querying all the door's entry and exit records, the more the door, the more set Easy, easy management.
At the same time, the access control system can communicate with the computer, and the access control management software installed on the computer is used to set the permission of the card and check the access record of the access control. Without using a computer, the system can also run normally offline. The software can be used to set permissions and parameters. It can monitor the entrance and exit conditions of various doors in real time and create statistical attendance reports. Easy setup, easy management, and greater security.
HID Global iCLASS? Non-contact card technology has become the industry standard for high-frequency smart card technology. In 2002, HID Global introduced the first generation of iCLASS technology, extending the advantages of proximity cards to a more powerful and versatile platform, with the same reliability, convenience and cost-effectiveness. At the same time, this platform can be used for data encryption and mutual authentication. Provide more security.
To make the access control system more powerful, HID iCLASS 13.56 MHz contactless smart card technology and read/write fields are interoperable and support a variety of applications such as biometric authentication, microelectronics payments, and PC security login. The iCLASS technology platform has provided reliable services for nearly 10 years. Together with the multitechnical multiCLASS solutions adopted by HID Global, it has become the standard for efficient, safe and effective access control systems.
Entering the era of NFC With the evolution of the times, access control systems are moving toward virtualization and mobility. Near Field Communication (NFC) is a technology that is applicable to access control systems. This short range wireless communication standard enables data exchange between devices within a few centimeters. NFC also fully complies with the ISO standard for managing contactless smart cards, which is a significant feature of its ability to become an ideal platform. By using a mobile phone equipped with an NFC technology to carry a portable ID card and then reading it wirelessly by a card reader, the user can show the phone in front of the card reader to open the door. According to research firm IHS iSuppli, in 2015, manufacturers will ship around 550 million NFC-enabled handsets.
The simplest mode of NFC virtual credential card is to copy the access control principle in the current card. The mobile phone passes the identity information to the reader, which in turn sends it to the existing access control system and finally opens the door. In this way, without using a key or smart card, a safer, more portable way to configure, monitor, and modify credential security parameters is eliminated, eliminating the risk of the credential being copied and temporarily distributing the credential if necessary. If lost or stolen, you can cancel the card. HID Global's iCLASS SIO technology-enabled (SE) platform is the first to provide and manage security authentication through the introduction of a technology-independent Secure Identity Object (SIO) virtual credential card.
Virtual credentials cards containing identity information can be embedded in a variety of portable devices, including NFC smartphones, microprocessor-based SmartMX cards, enabling access control technology applications beyond the traditional card and reader modes, with virtual credentials The card uses the phone as an access card. As a result, the access control technology used in the past decades can now be embedded in mobile devices such as mobile phones. When we open the door, we no longer need keys and cards. We only need to read mobile phones with NFC capabilities and built-in virtual credentials cards. Before the card reader, you can open the access control.
The advantage of iCLASS SE's virtual credential card technology lies in its portability and better system security. The SIO Virtual Credential Card provides additional diversification keys for data, authentication and encryption and encryption functions to prevent security breaches. This security performance of SIO binds data to specific devices according to the unique characteristics of the device, preventing the SIO from being copied to another device, thereby preventing copying cards from being invaded in various places. SIO virtual credential card in HID
Global Trusted Identity Platform? Operating within the framework (TIP?), the framework establishes a secure and trustworthy boundary for the secure submission of keys in access control applications based on SIO technology. The TIP framework provides a convenient way to securely configure the SIO virtual credential card on various platforms such as mobile devices. No matter where the user is or what kind of network connection is used, there is no problem.
In addition, SIO technology supports remote configuration and management. For example, SIO mode provides secure remote management functions. If a user's mobile phone is lost, these management functions can be used to securely and easily configure, monitor, and modify the security parameters of a virtual credential card, thereby eliminating the possibility of copying a virtual credential card and temporarily issuing new ones. Virtual credential card and revocation of lost or stolen virtual credential card.
March 08, 2024
November 29, 2023
E-mel kepada pembekal ini
March 08, 2024
November 29, 2023

Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.

Fill in more information so that we can get in touch with you faster
Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.