
Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.
86-0769-39020536
This paper describes the hardware circuit and software design framework of STM32 with Cortex-M3 core as the main control chip, RF chip PN532 and Ethernet controller ENC28J60. At the same time, the Ethernet protocol LwIP is analyzed in detail. The access control system has a long transmission distance, ultra-low power consumption, excellent performance and stability, and is fully applicable to the campus and the company's access control system.
introduction
At present, there are many enterprises that use the work permit to complete the access control management, and still use the traditional manual method to complete, not only easy to be mixed in, and there is no record, there are various human errors. At the same time, the access control system in the market has problems such as limited transmission distance and poor performance.
With the rapid development of embedded technology and the popularity of Ethernet technology, more and more embedded products based on Ethernet are developing faster and faster. This paper studies the access control system that combines Ethernet transmission data and RF chip identification smart card. Compared with the traditional access control system, Ethernet solves the problem of transmission distance. Secondly, the RF chip PN532 based on the 80C51 core is used to make the performance more stable. The basic principle of its work is to put the smart card on the access control system. The system reads the data and transmits it to the main chip STM32 for processing. After the main chip is processed, the data is transmitted from the ENCN8J60 to the server through the Ethernet protocol LwIP.
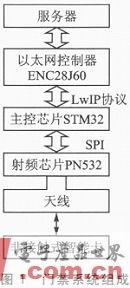
1 access control system hardware components
The access control system is mainly composed of STMicroelectronics' main control chip STM3H, Microchip's Ethernet controller ENC28J60 and NXP's RF chip PN532.
The structure of the access control system is shown in Figure 1. The main chip STM32 transmits data to the ENC28J60 through the Ethernet protocol stack LwIP, and then can communicate directly with the server through the network cable, or can be connected to the server through the router. In the case of contactless card communication, the STM32 is connected to the PN532 via an SPI interface with a frequency of 1 MHz.
1.1 STM32 peripheral circuit design
This system uses STMicroelectronics' Cortex-M3 core 32-bit microprocessor STM32F103 as the main control chip, its main frequency is 72 MHz, the internal integrated storage space is 256K Flash and 64K SRAM, also includes I2C, SPI , I2S, USART, CAN, ADC, watchdog, etc. The price/performance ratio is very prominent in similar products. The hardware connection is shown in Figure 2.

We use SWD instead of JTAG during debugging because SWD not only has fewer pins, but is also more reliable in high speed mode.
1.2 RF chip PN532 hardware circuit design
The PN532 is a highly integrated contactless read/write chip from NXP that includes the 80C51 microcontroller core and integrates various active/passive contactless communication methods and protocols at 13.56 MHz. Support ISO14443A/14443B protocol. Working distance is over 75 mm. A signal from the antenna is received and the data is processed in accordance with the frame format specified by ISO 14443.
The PN532 supports three communication methods: SPI, I2C, and HUS. Since we use the SPI method to communicate with the master chip STM32, I0 and I1 are set to 0 and 1, respectively.
The peripheral circuit structure of PN532 is shown in Figure 3.

1.3 Ethernet controller ENC28J60 hardware design
The main control chip ENC28J60 is an independent Ethernet controller with an industry standard Serial Peripheral Interface (SPI). It can be used as an Ethernet interface for any controller equipped with an SPI. The ENC28J60 complies with all IEEE802.3 specifications and employs a range of packet filtering mechanisms to limit incoming packets. It also provides an internal DMA module for fast data throughput and hardware-supported IP checksum calculations. Communication with the host controller is accomplished through two interrupt pins and SPI with data rates up to 10 Mb/s.
Two dedicated pins are used to connect the LEDs for network activity status indication.
It should be noted that when reading a plurality of data from the ENC28J60, even if the data output from the master chip STM32 is not required, a data is written to the SPI transmission buffer to start the interface clock of the SPI before each data is read.
The typical application circuit of ENC28J60 is shown in Figure 4.

2 system software design
2.1 Ethernet Protocol LwIP
LwIP is a small open source TCP/IP protocol stack developed by the Swiss Academy of Computer Science. Since it only needs a dozen K of RAM and a ROM of about 40K to run, it is suitable for use in embedded systems where hardware resources are not sufficient.
LwIP is a loose communication mechanism that implements communication between the application layer and the underlying protocol by means of shared memory. It provides three APIs: 1RAM API, 2LwIP API, and 3BSD API.
The disadvantage of the RAM API is that the code is not easy to understand, and the development is difficult. The advantage is that it consumes less resources and is more efficient than the other two methods, and is more suitable for embedded use with relatively few resources, so we use RAM. The API method is written.
There are two protocols, TCP and UDP, in the TCP/IP transport layer. TCP provides reliable transmission of data in an IP environment, and UDP provides unreliable transmission. Since the access control system must require correct data transmission, TCP is used. Figure 5 is a block diagram of the TCP processing flow under LwIP.
The RAM API puts the protocol stack and applications in a process based on function callback techniques. Below are some of the key configuration and code for LwIP.
(1) LwIP configuration
Modify the following places in the LwIP configuration file lwipopts.h.
Whether to use the operating system, we don't need it, so fill in as 1:
#define NO_SYS 1
Configure the size of the heap:
#define MEM_SIZE
Configure the size of the pool
#define PBUF_POOL_SIZE
#define PBUF_POOL_BUFSIZE
The above three configurations occupy most of the memory of the LwIP protocol stack, and need to be modified to an appropriate value according to their needs.
(2) LwIP code
1 Set the IP address, subnet mask and gateway separately:
IP4_ADDR(&ipaddr,192,168,2,28);
IP4_ADDR(&netmask,255,255,255,0);
IP4_ADDR(&gw,192,168,2,254);
2 Initialize the underlying function, that is, configure the MAC address, initialize the ENC28J60, configure the maximum output unit, etc.:
Low_level_init(netif);
3 Connect to the remote host, when the connection is established, the fourth parameter Conn_Back will be called:
Tcp_connect(TCP_pcb,&ipaddr,1026,Conn_back);
4 Callback function called when new data is received:
Tcp_recv(TCP_pcb.tcp_recv_callback);
5 Callback function called after the server successfully receives the data:
Tcp_sent(TCP_pcb,tcp_sent_callback);
6 handle the wrong callback function:
Tcp_err(pcb,CMD_conn_err);
7 Whether the data is received:
Ethernetif_input(&enc28j60);
Once the communication is over or an abnormal condition occurs, be sure to use the pbuf_free() function to release the pbuf to avoid wasting memory. It is also important to note that the timer functions tcp_fasttmr() and tcp_slowtmr() functions must be called regularly at regular intervals during normal operation.
2.2 Access Control System Software Architecture and Design
The main flow of the access control system is shown in Figure 6. After each restart, first initialize the relevant registers, initialize each module, determine that the server has been connected, and then enter the main loop of the program.

First, it is necessary to monitor whether it is necessary to call the fast timer and the slow timer inside LwIP. Then, it is monitored whether the server is disconnected. If it is disconnected, the server is reconnected. If there is no disconnection, it detects whether there is a smart card. In some cases, the information in the receiving card is processed and then sent to the server.
Conclusion
This paper describes the hardware and software architecture of the access control system using STM32 as the main control chip. It has guiding significance for the use of the chip and Ethernet protocol involved in the paper, which can greatly reduce the cost, and at the same time, the access control system The use will be more stable and the transmission distance will be longer.
March 08, 2024
November 29, 2023
E-mel kepada pembekal ini
March 08, 2024
November 29, 2023

Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.

Fill in more information so that we can get in touch with you faster
Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.